Xiphera expands its Elliptic Curve Cryptography (ECC) portfolio with two new IP cores: XIP4123C and XIP4133C (together referred as XIP41x3C). Both of these IP cores support Elliptic Curve Diffie-Hellman (ECDH) key exchange and Elliptic Curve Digital Signature Algorithm (ECDSA) digital signatures. XIP4123C implements them on the NIST (National Institute of Standards and Technology) P-256 elliptic curve and XIP4133C on the NIST P-384 curve defined by in FIPS PUB 186-2, 186-3, 186-4, and 186-5. These two curves are arguably the most widely-used elliptic curves nowadays and, therefore, the XIP41x3C IP cores complement Xiphera’s existing ECC IP cores that support X25519 key exchange and Ed25519 digital signatures.
XIP41x3C family of IP cores are versatile IP cores that have applications in several cryptographic protocols and systems. ECC on NIST P-256 and/or P-384 is used, for example, in TLS 1.2 and TLS 1.3, IPsec IKEv2, and numerous other protocols. The world of asymmetric cryptography is experiencing a major change in the coming years when Post-Quantum Cryptography (PQC) is being adopted. Despite the emergence of PQC, also ECC has an important role to play in the future in hybrid systems combining PQC and ECC. These hybrid systems will provide security against attacks even in the case if weaknesses are found from the new PQC cryptosystems. In Xiphera’s webinar, The Role of Elliptic Curve Cryptography in the Post-Quantum Era, we discuss this topic at a deeper level.
The resource footprint of XIP41x3C cores has been carefully optimised and they require only about 1000 6-input LUTs, 1-2 hardwired multiplier(s), and a few embedded memory blocks on a typical modern FPGA device. These impressively small numbers allow our customers to integrate ECC functionalities even in congested designs in small FPGA devices. Despite the small resource usage, XIP41x3C can still perform several cryptographic operations in one second: for example, one ECC key generation takes 21.5 ms on NIST P-256 when XIP4123C is clocked at 200 MHz. This level of performance is sufficient for most ECC use cases, for example, in industrial automation or highly secure systems.
Various features for improved security
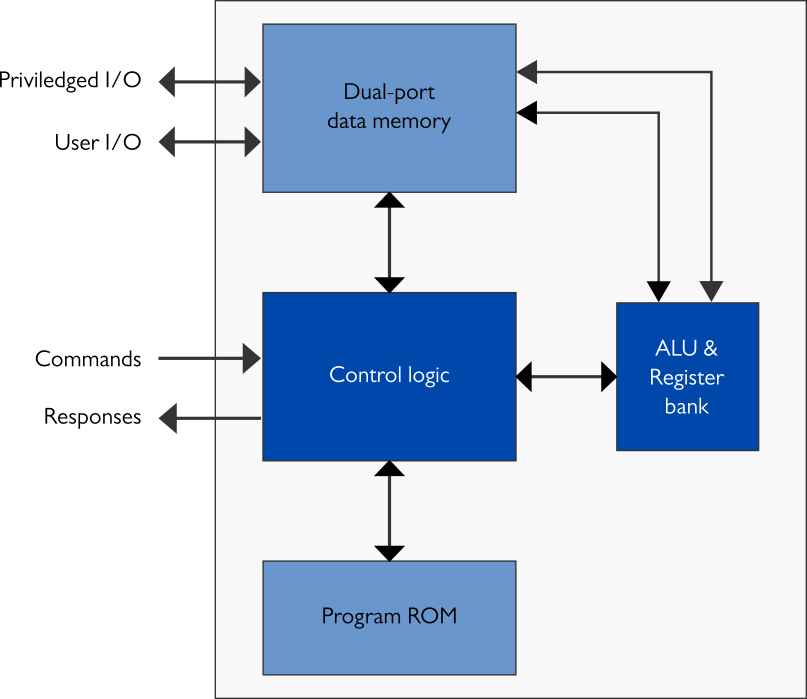
XIP41x3C cores include many features that guarantee secure design of the systems. As an example, there are two different interfaces so that only one of them has access to the secret values used in ECDH and ECDSA. This allows, for example, to design systems where XIP41x3C can be used for signing documents without the signer having access to the secret signing keys. XIP41x3C also have a strong level of protection against side-channel attacks. In particular they have fully constant latencies for all operations that use the private keys and they are fully protected against all timing attacks as a consequence.
“ECC has become the de facto standard for implementing asymmetric cryptography during the last decades and the NIST prime curves are the most widely-adopted ways to implement ECC. Although new PQC will be taken into use in the coming years, ECC will still be important for years to come and this is why we at Xiphera decided that it is important to extend our ECC portfolio with efficient and – most importantly – very secure IP cores for ECC on NIST prime curves”, says Kimmo Järvinen, Co-founder and CTO of Xiphera.
For more information, visit the product page of XIP41x3C. You can also view and download the product brief. Don’t hesitate to contact us via our website or by sending us email to sales(at)xiphera.com.
Xiphera’s webinar: The Role of Elliptic Curve Cryptography in the Post-Quantum Era
Dr. Kimmo Järvinen, Xiphera’s co-founder and CTO, talks about the importance of secure implementation of Elliptic Curve Cryptography (ECC). Although the world of cryptography is moving to Post-Quantum Cryptography (PQC), ECC still has a significant role to play also for years to come in hybrid systems that combine PQC with ECC.
Even though ECC is already mature technology, its implementation is never a simple task and even small implementation mistakes can lead to major security problems, as has been seen even lately. This webinar discusses how to avoid pitfalls of ECC implementations and the role of ECC in future cryptosystems.
Missed this webinar? Find the full recording and the presentation slides here.
If you want receive information about upcoming webinars, sign up for Xiphera’s webinar subscription list here, and you’ll never miss any of our fascinating webinars!