Secure Hash Algorithm 3 (SHA-3)
Xiphera’s CAVP-validated compact and high-speed SHA-3 IP cores, using Secure Hash Algorithm 3, are designed to verify the integrity of the data.
About the product
Hash functions are essential building blocks for many cryptographic protocols. They are used to verify the integrity of the data i.e., to verify that the data sent was not modified on the path. Secure Hash Algorithm 3 (SHA-3) is a family of hash functions that NIST has standardised in FIPS PUB 202 in August 2015.
Xiphera offers two primary versions of SHA-3 implementations: a compact IP core and a high-speed IP core. The main functionality of these IP cores is to calculate a SHA-3 message digest (also commonly known as a hash value). Both SHA-3 IP cores have received CAVP validations. The CAVP certification of our IP core assures its compliance with rigorous cryptographic standards.
What distinguishes our SHA-3 IP cores is their device-agnostic design, which enables them to be compatible with a broad spectrum of FPGA and ASIC platforms. Additionally, our SHA-3 IP cores offer robust protection against timing attacks, as their execution time remains unaffected by input values, ensuring enhanced security. It is also worth noting that our IP cores proudly support NIST Special Publication 800-185.
Xiphera offers the following versions of SHA-3 IP core:
1. Versatile SHA-3-224/256/384/512 and (c)SHAKE-128/256 IP core, compact variant (XIP3030C)
2. Versatile SHA-3-224/256/384/512 and (c)SHAKE-128/256 IP core, high-speed variant (XIP3030H)
Both our SHA-3 IP cores are designed for versatile support of all variants of the SHA-3 hash function and related extendable-output function SHAKE as well as the SHA-3 derived function cSHAKE and its variants KMAC, TupleHash,and ParallelHash (including their arbitrary-length output variants). The interface of both the offerings is pin-wise compatible with each other. Additionally, they also support NIST Special Publication 800-185 by supporting cSHAKE-128 and cSHAKE-256 XOFs. The only differences are in performance (latency) and resource requirements. Applications that require high-speed hashing can benefit from our high-speed SHA-3 IP core which is optimised for maximum speed.
Key features
- Versatile Algorithm Support: Xiphera’s SHA-3 IP cores
support SHA-3-224/256/384/512, SHAKE-128/256, and cSHAKE-128/256.
- Secure Architecture: The execution time of Xiphera’s SHA-3 IP cores is independent of the input values and, consequently, provides full protection against timing-based side-channel attacks.
- Standard Compliance: Xiphera’s SHA-3 IP cores are compliant with FIPS 202 and SP 800-185. They can be used as a part of numerous systems and protocols that require SHA-3 or its derivatives.
- Easy Integration: The 64-bit interface of Xiphera’s SHA-3 IP cores supports easy integration to various systems.
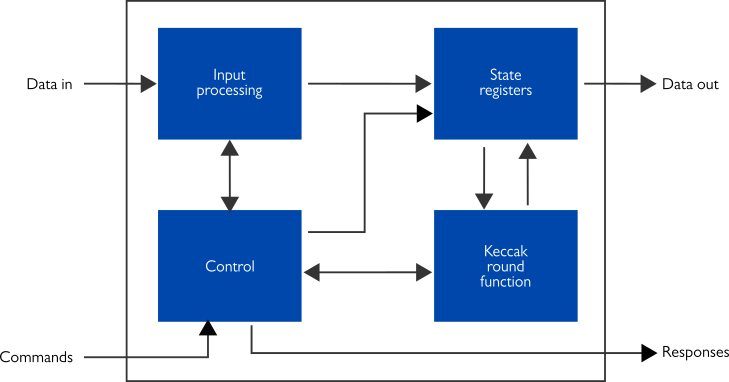
For more details, including FPGA resources & peak performance as well as ordering instructions, open the full product briefs in PDF. Contact us here, and we’ll get back to you as soon as possible.
Interested to learn more about the technical details and performance numbers for ASIC application? Register for the ASIC-specific product brief here.
Partner collaborations
We are proud partners with leading global as well as innovative growing FPGA companies. We offer a selection of our cryptographic IP cores for our technology partners. Visit our partner pages to learn more about our SHA-3 offering for our partners.
