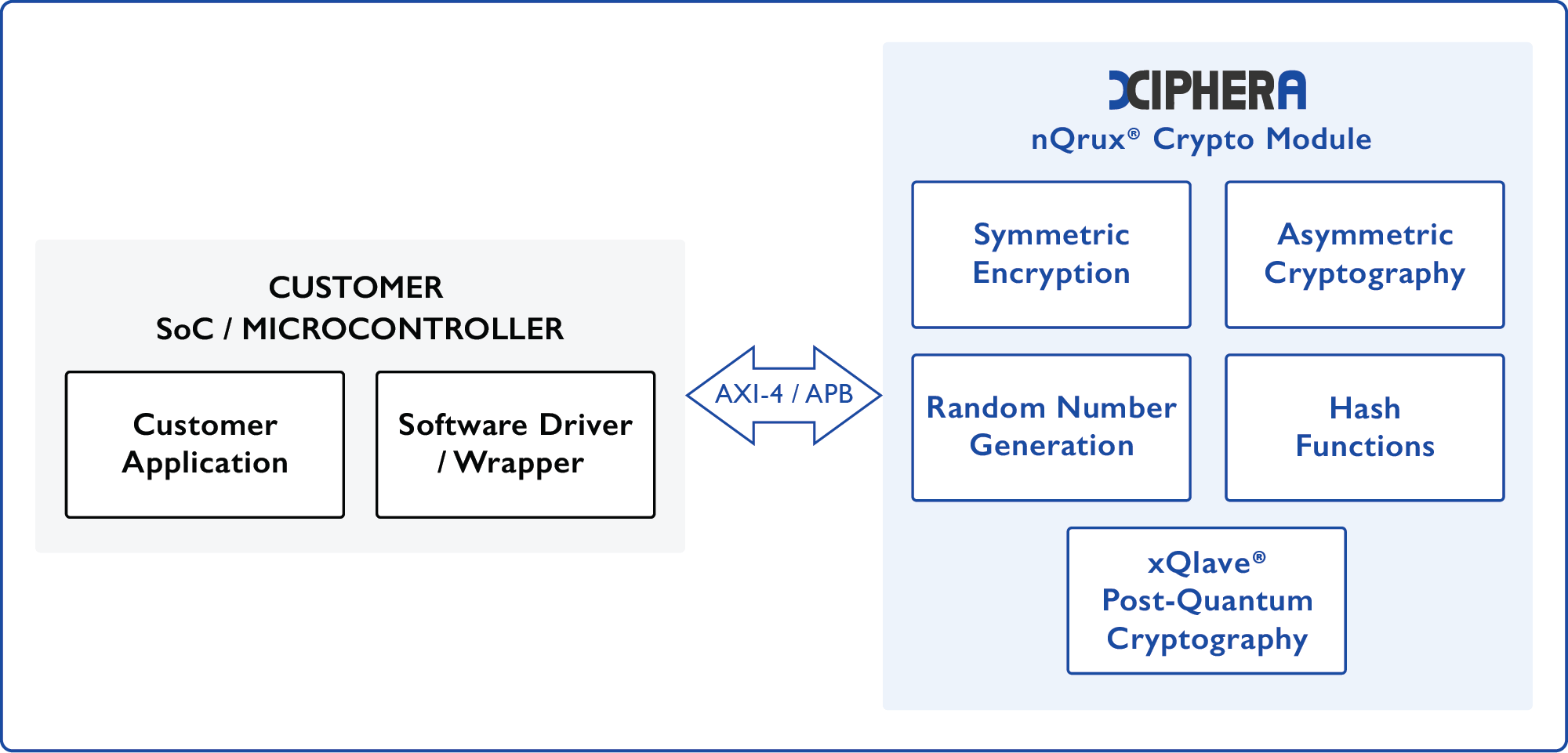
nQrux® Crypto Module
Offload and accelerate cryptographic algorithms for...
HW root-of-trust, secure boot, and security modules
Securing communication and data at rest
Key generation, management, and storage
Cryptographic co-processor for SoC
Key features
Customisable security platform
Optimised for microcontrollers & SoCs
Comprehensive data protection
Robust encryption & hashing
Quantum-secure crypto option
Pure RTL with no hidden CPU or software
Industry standard compliance
Efficient and optimised architecture
Easy system integration
Vendor agnostic FPGA/ASIC implementation
Selectable IP cores
xQlave®– Post-Quantum Cryptography
Symmetric Encryption
Hash Functions
SHA-3
Product codes: XIP3030C (CAVP-validated), XIP3030H
HKDF/HMAC/SHA-256
Product code: XIP3322B (CAVP-validated)
HKDF/HMAC/SHA-384
Product code: XIP3323B
HKDF/HMAC/SHA-512
Product code: XIP3324B (CAVP-validated)
HKDF/HMAC/SHA-256/512
Product code: XIP3327C (CAVP-validated)
Asymmetric Cryptography
ECC Accelerator
Product code: XIP4200H
NIST P-256/P-384 ECDH and ECDSA
Product code: XIP41X3C (CAVP-validated)
Curve25519 Key Exchange (X25519)
Product code: XIP4001C
Curve25519 Key Exchange and Digital Signatures
Product code: XIP4003C
RSA Signature Verification
Product code: XIP5012C
Random Number Generation
True Random Number Generator (TRNG)
Product code: XIP8001B
Pseudorandom Number Generator (PRNG)
Product codes: XIP8103B, XIP8103H (CAVP-validated)
Find more technical details, including FPGA resources & peak performance as well as ordering instructions, from the product brief.
Critical security for unified and isolated HW solutions
Cryptographic modules offer an all-inclusive cryptography package for customised security needs. Let’s deep-dive into the benefits, implementations, and possible use cases of a hardware-based cryptographic module.

