Let us use as an example of TCP/IP operation over Ethernet the use case of Terminal program PuTTY with an opened session to IP address 192.168.1.64 port 25.
The user types “Hi!” and PuTTY passes that string with Telnet-protocol to the application layer. The application layer passes data to the right session on the transport layer.
On the transport layer, the destination port 25 is added to the TCP frame, and additional fields (sequence number) etc. are updated.
Next on the Internet layer, the IP header is added to the packet and the destination IP field is filled with value 192.168.1.64 in this example case.
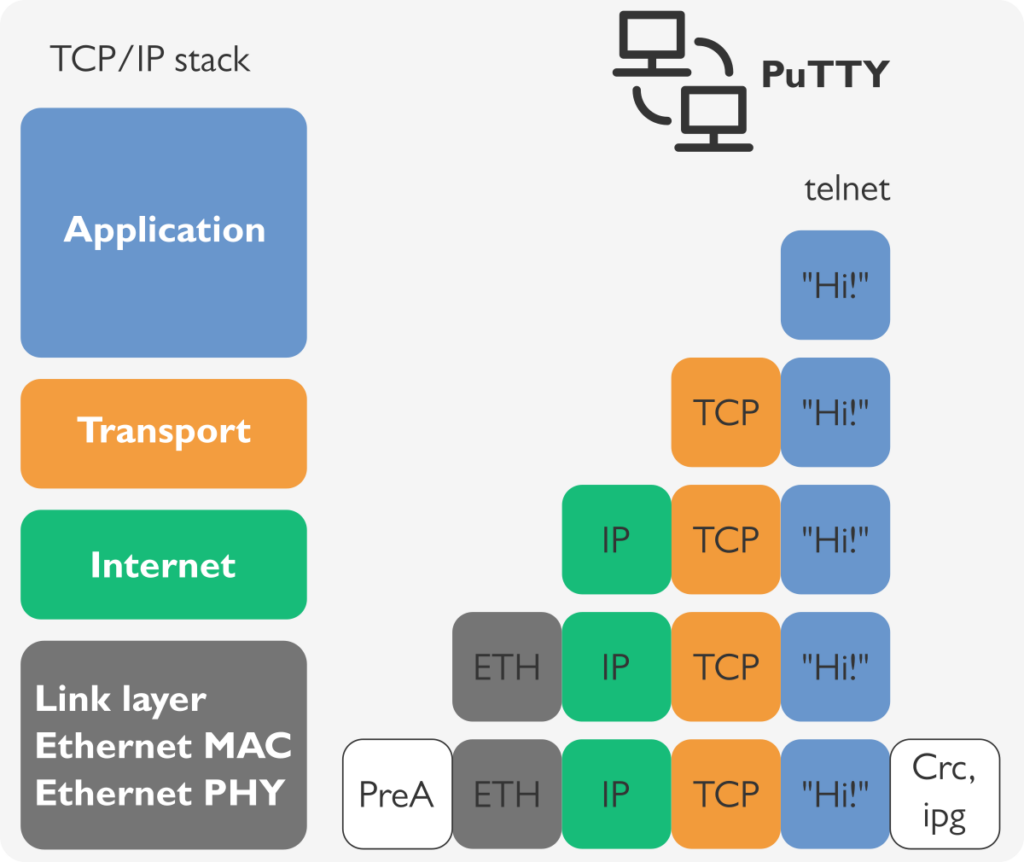
Next the packet is sent to the Link layer, where the Ethernet header is added to the packet. The Ethernet header contains destination and source Ethernet MAC addresses and length/type of frame. The Ethernet MAC (Media Access Controller) adds preamble and start of packet indicator before the frame and calculates the CRC-32 checksum & interpacket gap after the packet.
At the receving end, the operations described above are reversed and the telnet server receives only data “Hi!” the from application layer in its session with the client.
We can compare this to sending a postcard:
- Selecting a postcard = selecting the application for communication.
- Writing a message on the postcard = sending data, “Hi!”
Filling in the address information
- Name = TCP header
- Address = IP header
- Zip and Town = Ethernet header
Gluing the stamp onto the postcard and dropping the postcard into the mailbox = delivery method selected.
The postal service will perform their task and delivers the postcard to the destination = routing.
The postcard will be delivered to a postal routing center, the destination postal area is selected based on the zip value and finally the postman drops the postcard into the receiver’s mailbox. During this process, less and less address information is needed as the postcard approaches its destination. This can be compared with going up on TCP/IP stack from the link layer to the application layer.
Return to the article ‘MACsec protects your critical point-to-point communications’.



