Xiphera’s comprehensive MACsec solution portfolio protects both the confidentiality and integrity of data transmitted on a point-to-point communications link. To understand the use cases and applicability of MACsec, a brief overview of a layered communications model as specified in the OSI model is needed.
OSI model explained
Open System Interconnection model, or the OSI model, was formalised by International Organisation for Standardisation in 1984. The purpose of the OSI model was to provide a set of design standards to allow communication between computers from different manufacturers (for example between Windows PC and Apple iMAC).
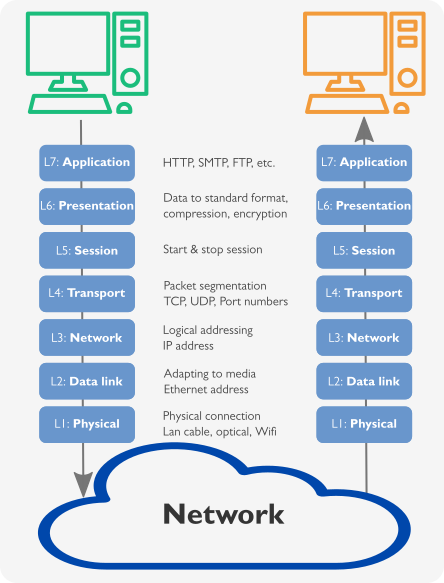
The OSI model defines seven layers described in the first picture on the right. Transmitted data goes from layer 7 to layer 1 and on receiving end from layer 1 to 7.
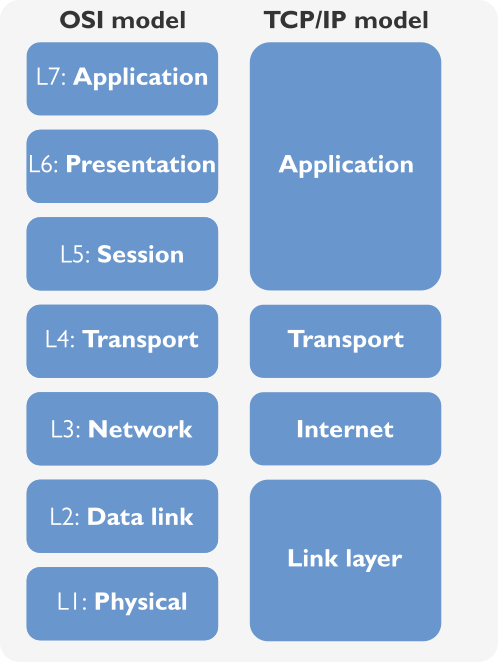
The real-world implementation is not precisely following the layers of the OSI model. Today, most of networks use TCP/IP protocol (Transmission Control Protocol / Internet Protocol), which has a slightly different model. Originally RFC1122 defines four TCP/IP layers (in the second picture on the right), but certain textbooks also talk about three or even five layers.
The number of layers and how they are implemented are not as formally defined in the TCP/IP protocol. Typically Ethernet interface is used, and it is divided into L1 (Ethernet Physical layer) and L2 (Ethernet Media Access Control layer) according to the OSI model.
Click here to see an example of TCP/IP operation over Ethernet.
“TCP/IP protocol itself does not quarantee security,” says Xiphera’s System architect, Tuomo Tarvainen. “If someone can have access to your TCP/IP traffic, your data is visible within network.
“There are solutions for secure internet access: TLS 1.x, IPSEC, OpenVPN, MACsec to name a few. Most of the implementations of these protocols are software-based. However, Xiphera focuses on hardware-based implementations of security protocols as they offer better performance and increased security level.”
Enhanced security with Xiphera’s MACsec solutions
MACsec is a point-to-point protocol in the second layer of the OSI model. The confidentiality and authenticity of transmitted data is protected by AES (Advanced Ecnryption Standard) in GCM (Galois Counter Mode) with either 128 or 256 bits long keys. The underlying crypto engines in Xiphera’s MACsec solutions are based on Xiphera’s own AES-GCM IP (Intellectual Property) cores.
Xiphera’s MACsec solutions are available in both Balanced (‘B’) and high-speed (‘H’) versions, and their Field Programmable Gate Array (FPGA) logic resource usage ranges from 16000 LUTs (lookup tables) to 55000 LUTs.
MACsec is typically used in high-speed networking applications, where an individual communications link to be protected has a bandwidth from 1 Gbps (gigabits per second) up to 40 Gbps. Even higher bandwidths can be achieved by using several MACsec IP cores in parallel.
In certain cases, Xiphera’s MACsec solutions can also be retrofitted into an existing system, especially if there is already an FPGA with enough available logic resources.
MACsec has found many new applications in addition to its original use case of protecting communications in wired local area networks. MACsec can for example be used to protect critical control messages in communications networks, or to protect sensitive measurement data in industrial automation applications. Other potential use cases are secure point-to-point video links.
Tarvainen agrees with the good applicability of the solution: “Xiphera’s hardware-based MACsec solutions provide better protection against common software-based attacks, since all critical security information is stored in the FPGA. Hardware-based MACsec solutions also have better performance, higher throughput, and lower power consumption compared to software-based solutions with high data rates.”