We spend hours and hours online. We send emails, play online games, sit in remote business meetings, browse the Internet… For these to happen, we are relying on seamless data flow every minute, every day. That’s why institutions worldwide have created standards for fluent communications – one of the most famous ones is the OSI model, which in order to be fully reliable needs proven security on its critical layers.
OSI model – what and why?
Open System Interconnection (OSI) model introduces the seven layers for device communications. It was developed in the 1980s for a standardised process of communications between different manufacturer’s computers (for example, between Windows and MacBook computers). Today, the OSI model can be implemented on two-way data flow between any devices. In the seven layers of the OSI model, the transmitted data goes from layer 7 to layer 1, gets transmitted via physical network (for example, through LAN, WLAN, Bluetooth, 5G, optical cable, etc.), and then at the receiving end, flows from layer 1 to 7 and finally to the receiving device/user.
In the real world, the data does not always follow precisely the seven layers of the OSI model. Today, many network communications use TCP/IP protocol (Transmission Control Protocol / Internet Protocol), where the protocol’s fewer layers compared to the OSI model are not as formally defined.
Seven layers of OSI model
OSI model introduces the following layers for the transmitted data flow:
- Physical layer, covering physical hardware elements such as cables, connectors, or network interface cards.
- Data Link layer, offering point-to-point communication between devices over network and managing access to the Physical layer; the most common example is Ethernet.
- Network layer, determining the best path for data to be transmitted between devices across multiple networks, typically using IP addresses.
- Transport layer, ensuring data integrity through end-to-end communication by segmenting data into smaller units.
- Session layer, creating and managing connections, or sessions, between applications.
- Presentation layer, ensuring data flow between the Session and Application layers to make the data usable for the topmost layer.
- Application layer, utilised by the end user, serving as the interface between network and user software (such as email, remote login, file transfer, web browser, etc.).
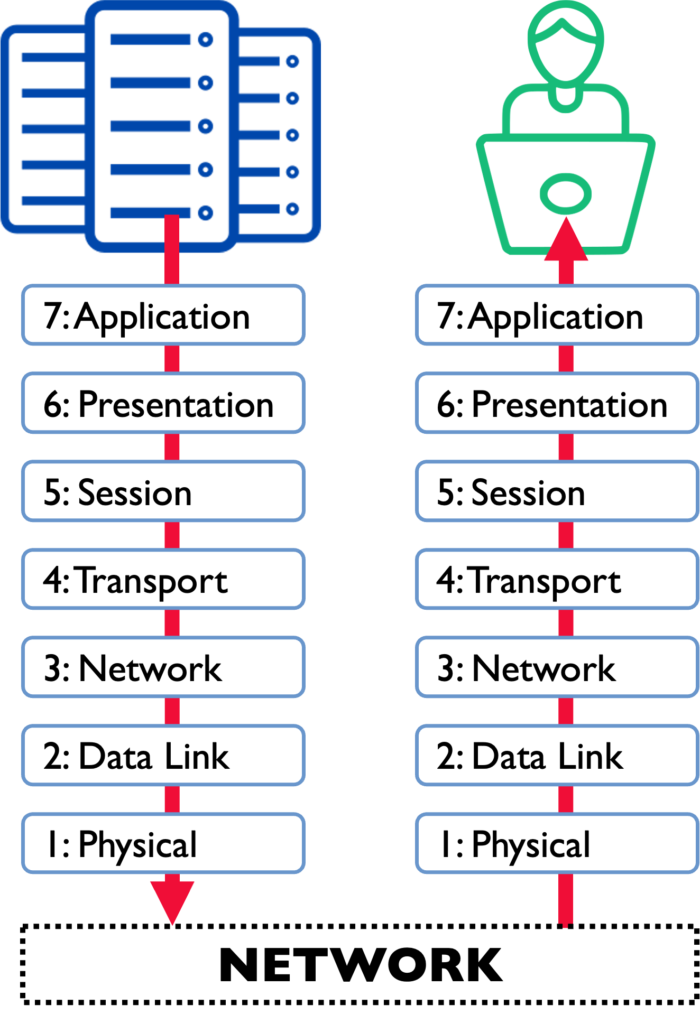
It is important to notice that the commonly implemented TCP/IP model introduces typically only 4 to 5 layers. These layers, however, follow a very similar pattern to the layers presented in the OSI model – the Transport, Internet, and Link or Network layers of the TCP/IP are in principle equivalent to the OSI model’s Transport (4), Network (3), and Data Link + Physical (1-2) layers, respectively, and the Application layer of the TCP/IP model covers the layers 5-7 (Session, Presentation, Application) layers of the OSI model.
How to secure data in the OSI model?
How can we be sure that the data transmitted to the receiving end has not been tampered with during its long and multi-phased journey from OSI layers 7 to 1 and back to 7? This is obviously a critical question in our contemporary world of cyber threats. During the first phase of both OSI and TCP/IP work data security and privacy were not taken into consideration, and the required security protocols were developed afterwards.
Naturally, like every communication, the data in the OSI model needs to be secured throughout its journey. Some layers are more prone to external threats than others. For example, the Application layer (7) of the OSI model is handled directly with end-user applications and services, making it a usual target for various cyber threats.
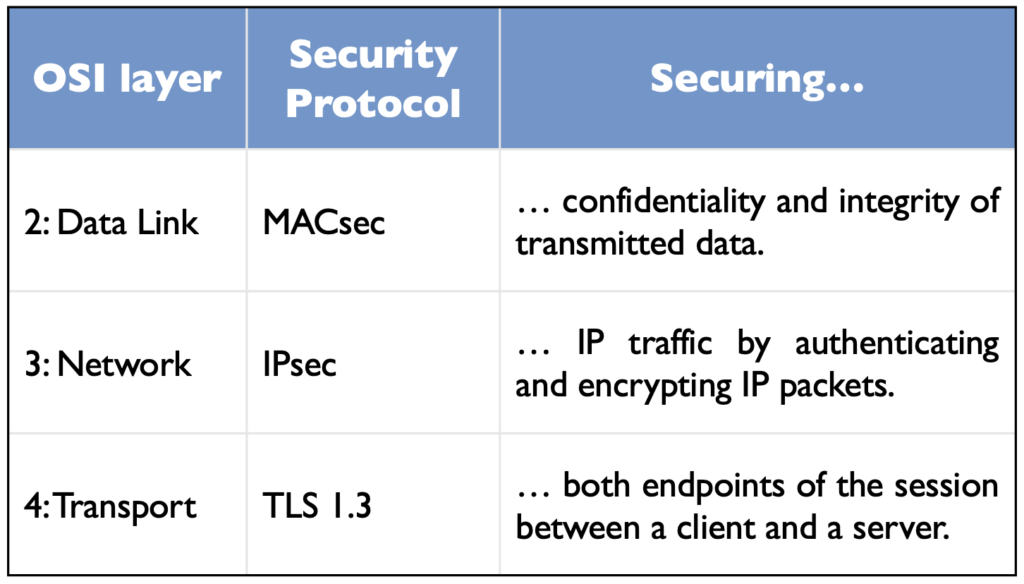
Layers 2 to 4 (Data Link, Network, Transport), being close to the network interface, are also critical to secure. The Data Link layer (layer 2) plays a pivotal role in defining secure communication between directly connected network devices. By securing the Data Link layer, we can affect the overall security of the network, by ensuring data integrity, preventing unauthorised access, and enhancing network performance. Data Link layer can be secured for example with MACsec (Media Access Control security), a point-to-point Ethernet security protocol, protecting both confidentiality and integrity of transmitted data.
The Network layer (3), being responsible for forwarding data between networks, is essential to secure for ensuring proper routing and IP address management, preventing unauthorised access or network attacks. A well-established security solution for the Network layer is IPsec (Internet Protocol security), securing IP (Internet Protocol) traffic by authenticating and encrypting IP packets within a communication session. IPsec is a widely used security protocol, and its importance in today’s hybrid work environment has increased with growing demand to secure the communications from e.g. our home offices.
The Transport layer (4) covers end-to-end communication, and maintaining the layer’s confidentiality, integrity, and authenticity is critical for ensuring secure communication. Securing the Transport layer guarantees that the transmitted data has not been corrupted or modified by unauthorised or unwanted parties. TLS (Transport Layer Security)protocol provides protection against these threats. The most recent version, TLS 1.3, establishes a secure connection between a client and a server over the Internet, thus securing both endpoints of the session.
Like the OSI model, these security protocols are constantly reviewed and standardised. Various international bodies, first and foremost IEEE (Institute of Electrical and Electronics Engineers) and the Internet community with their RFCs (Request for Comments) ensure that the security protocols used for protecting communications in the OSI model are up-to-date.
Securing OSI model with hardware-based security
To conclude, securing data flow in the OSI model is critical. The decision of which layers to secure depends on the context and specific security goals of the network. Nevertheless, it is important to always secure at least one layer of the OSI model.
Typically, enabling security for the layers 2, 3, and/or 4 of the OSI model ensures a high-security level of the communications. These layers, being close to the network interface, can be effectively secured with hardware-based security solution, such as MACsec, IPsec, and TLS 1.3 security protocols introduced above.
Hardware-based security, using cryptographic IP (Intellectual Property) cores, has several advantages compared to the software-based security approach. These include for example, higher security level, better performance and higher throughput for the applications, and lower power consumption than what would be achieved with a software-based security implementation.
Xiphera offers hardware-based security with cryptographic IP cores. Our extensive security portfolio covers security designs based on modern and standardised implementations of cryptographic algorithms directly into FPGAs and ASICs. Our Security Protocols family includes security solutions – MACsec, IPsec, and TLS 1.3 – for the most critical layers of the OSI model. These security protocols are typically implemented in conjunction with the commonly used TCP/IP protocol.
To learn more about how to secure your device communications with MACsec, IPsec, and TLS 1.3 – the three musketeers of Security Protocols protecting OSI model layers 2-4 – watch our webinar Cryptography at Work: Securing Device Communications.




