Modern day public key cryptography is largely covered by RSA and Elliptic Curve Cryptography (ECC). These are based on integer factorization and the discrete logarithm problem, respectively. In 1994, Peter Shor introduced a quantum algorithm capable of breaking both RSA and ECC. Luckily for digital security, quantum computers capable of running these attacks are still a long way down the road. However, with quantum technology advancing every year, this threat cannot be left to fester, and this looming vulnerability should be addressed as soon as possible. The solution? Post-Quantum Cryptography (PQC).
The National Institute of Standards and Technology (NIST) started a standardisation process for new PQC algorithms in December 2016. The third round of the competition concluded in July 2022, and out of 15 finalists four winners were selected: three signature algorithms and one key-encapsulation mechanism. At the same time NIST also announced an extra fourth round where a few Round 3 candidates are investigated further. The four winners, and possibly some Round 4 candidates, will be standardized in the upcoming years.
What this means in practice, is that in a couple of years we will start seeing PQC algorithms implemented on many devices. However, new and exciting does not immediately imply secure. In cryptography old and unbroken is far more reliable than new with no apparent flaws. For example, two contenders that made it to Round 3 of the NIST competition have been completely broken (Rainbow, SIKE). This is not to say that PQC is doomed and untrustworthy but rather a cautionary example that we should not abandon our old ways from the get go. Instead, the current recommendation (for instance by the National Cybersecurity Agency of France ANSSI) is to use a hybrid model.
Hybrid models are an intermediate step from the classical to the post-quantum
In a hybrid system, a new PQC algorithm is used in combination with some classical algorithm. When faced with a quantum adversary breaking classical algorithms, the hybrid system remains secure due to the PQC component. On the other hand, if some unknown exploit of the new PQC algorithms, with classical computers, were to arise, the tried and true classical component of the hybrid system would hold steady.
In theory, the hybridisation of classical and post-quantum is straightforward. For key-encapsulation mechanisms, the outputs of both algorithms is fed to a key derivation function to produce the key for symmetric encryption. For signatures, we sign the message twice: once with the classical signature and once with the PQC signature. Now the verifier only accepts the message if both signatures are valid. Concretely, these systems should be implemented with care and the specific use case in mind.
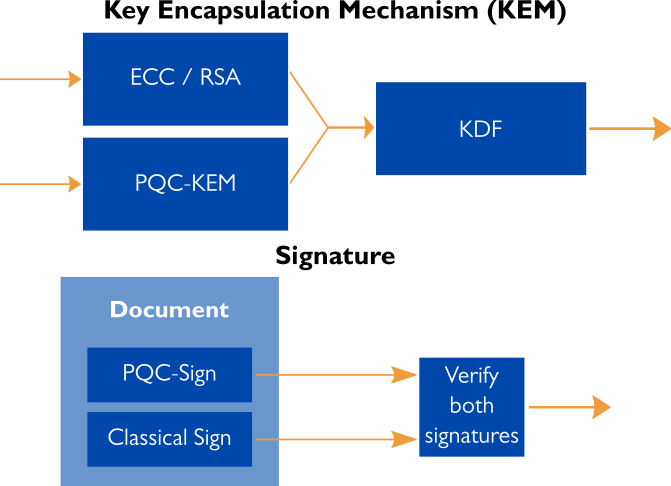
Hybridisation of course is not a permanent solution. Its purpose is to be an intermediate step in the migration from the classical to the post-quantum. As the years go by and no catastrophic attacks have come around, PQC becomes more and more reliable. In a decade or so, PQC could be implemented on its own.
Hybrid models are also very agile. They are modular combinations of different blocks. If one block would turn out to be faulty, it could be easily replaced with another one from the same family of algorithms. In particular, the re-programmability of FPGAs provides an excellent agile platform for this process. For example, consider a system with hardware components for ECC or RSA but with no support for PQC. A hybrid system could be built on top of the existing system by adding an FPGA with PQC support. Such hybrid solutions have critical importance as they allow extending the lifetime of already deployed secure systems.
Xiphera is actively following the development of PQC, and the first members of our upcoming PQC product family are scheduled to be announced in 2022. Xiphera’s PQC product line will be based on the PQC algorithms to be standardised by NIST and will support and complement our existing classical solutions, utilising the hybrid model. Xiphera’s existing product portfolio combined with our knowledge and development of PQC build a solid foundation for secure hybrid system design.
While PQC is under development, Xiphera’s classical algorithms can be found here.
Xiphera’s webinar: Post-Quantum Cryptography Round-Up – Where Are We Now and What’s Next?
Quantum computing opens new ways for perceiving computing and security. Although it will potentially offer solutions for difficult computational problems, it also poses a significant threat to data and communications security. The situation drives a development of security solutions against the quantum threat, and Post-Quantum Cryptography (PQC) is one of these solutions. The standardisation process of PQC took a big leap after National Institute of Standards and Technology’s (NIST) recent announcement of four PQC algorithms that will be included in the forthcoming PQC standard.
Mr. Perttu Saarela, Xiphera’s Developer, discusses the current status and future winds of PQC in Xiphera’s webinar, held on the 6th of September, 2022. He is working with research and development of PQC algorithms and has extensive knowledge and understanding of the topic.
This webinar introduces and reviews the current situation of PQC standardisation process as well as presents a clear summary of the selected standardisation algorithms, that can be complex and difficult to understand if not explained properly. Finally, we will give some guidelines to take into consideration when designing systems that must remain secure against the quantum threat for years to come.
Find the full recording of the webinar and presentation slides here.
If you want receive information about Xiphera’s upcoming webinars, sign up for Xiphera’s webinar subscription list here, and you’ll never miss any of our fascinating webinars!
Find all episodes of Xiphera’s webinar series Cryptography under the hood here.




