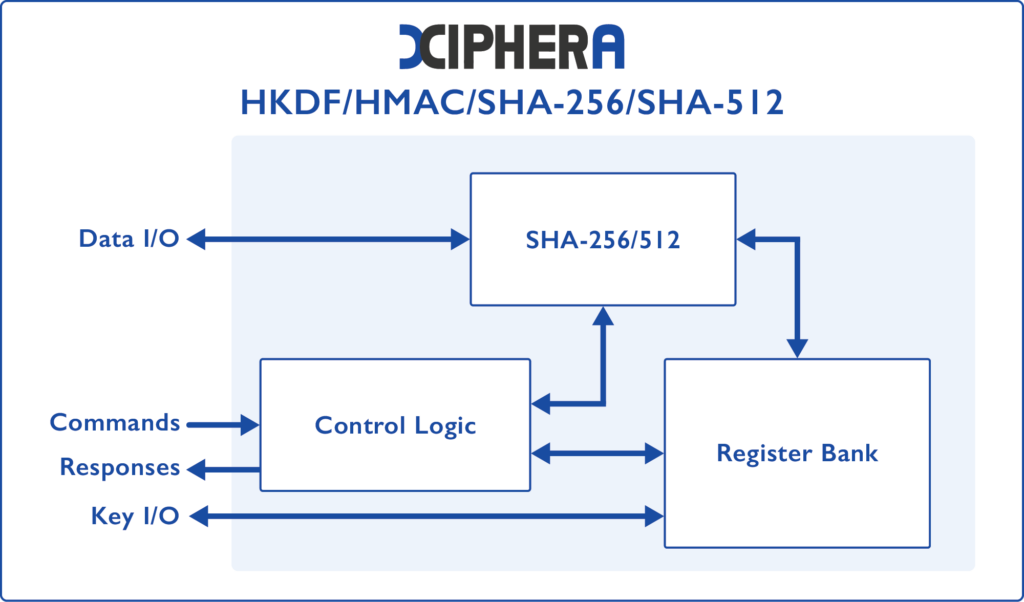
SHA-2 / HMAC and HKDF
Xiphera offers IP cores for key derivation with extended support for HMAC message authentication code and HKDF key derivation function.
Xiphera’s comprehensive hash function IP portfolio ensures the security and integrity of data through robust cryptographic standards. SHA-2 and Key Derivation Function IP cores provide versatile functionality for various applications, from data integrity verification to cryptographic key generation and security. The IP cores are powered by Xiphera’s in-house designed IP cores and are optimised for efficiency and high performance in FPGA and ASIC implementations.
Boost your security with advanced hash functions for…
Data integrity verification
Digital signatures
Blockchain transactions
Key derivation
Key features
- Optimised resource requirements
- Constant latency
- Compliant with relevant NIST standards
- CAVP validated by NIST
- Pure RTL without hidden CPU or software components
- Efficient and optimised architecture
- Easy system integration
- Vendor agnostic FPGA/ASIC implementation
Technical specifications
Support for SHA-256, SHA-384, and SHA-512. All variants have support for HMAC and HKDF.
Balanced SHA-256
Product code: XIP3322B
- 100s of Mbps
- From 1.4 kLUTs (FPGA)
- CAVP validated IP core
Balanced SHA-384
Product code: XIP3323B
- 100s of Mbps
- From 2.9 kLUTs (FPGA)
Balanced SHA-512
Product code: XIP3324B
- 100s of Mbps
- From 2.8 kLUTs (FPGA)
- CAVP validated IP core
Compact SHA-256/512
Product code: XIP3327C
- 10s of Mbps
- From 1.2 kLUTs (FPGA)
- CAVP validated IP core
Product brief
Learn more about the key features and functionalities of the SHA-2 / HMAC and HKDF IP cores.
Resource sheet
Download the resource sheet to learn more about the FPGA and ASIC resource requirements and performance.
Secure Hash Algorithm SHA-3
Xiphera’s portfolio of hash algorithms includes a SHA-3 IP cores, providing versatile functionality for various applications, from data integrity verification to password security.