Why do we need cryptographic modules?
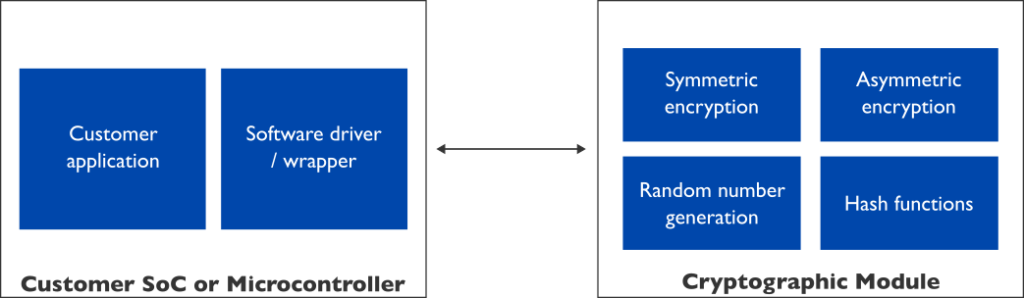
Securing data and communications, within and between microcontrollers, System on Chip implementations, and other systems, requires a range of cryptographic operations. These services include hash functions for ensuring data integrity, symmetric encryption for encrypting bulk data in transit or at rest, asymmetric encryption for key exchange, signing data and messages, as well as authenticating components, users, and accounts, and finally a source of quality randomness for cryptographic key generation.
Implementing all of these securely and in an optimised manner for a hardware platform requires in-depth skills and understanding of both cryptography and digital design for microcircuits. The various cryptographic services can be implemented, and are typically offered, as distinct IP cores dedicated to a single specified cryptographic algorithm. Additional logic and integration will need to be implemented around these IP cores to facilitate the necessary cryptographic operations and processes required by the surrounding total solution. Complexity of the system increases attack surface and the risk of design flaws and security vulnerabilities.
For these reasons, critical security services are often segregated into a single cryptographic module, behind a unified and well-defined interface for access by the rest of the system. This introduces a cryptographic boundary, which isolates security critical operations from the rest of the system.
Implementing cryptographic modules securely (today and tomorrow)
In designing a cryptographic module, it is critical to ensure that the module architecture is efficient, to limit access behind a unified, well-defined, and secure interface, and to minimise total attack surface. Module composition (selection of the provided security services, algorithms, and key lengths), as well as the optimisation of the implementation (area vs. performance), can be done according to system and industry requirements (e.g. for IoT, industrial, data centre, hyperscaler, telecommunications, space, or automotive use).
The most secure and efficient way to implement a cryptographic module for hardware is to ensure it is directly designed in hardware as digital logic. This method removes dependency on a multi-layered software technology stack with increased attack surface and potential for design flaws and vulnerabilities. Avoiding embedded CPU and its software components has benefits for performance and power consumption – and most critically, for security. Streamlining the architecture, defining a clear cryptographic boundary, and removing software and CPU components from the design also enable more straightforward and cost-effective validation and certification processes.
Hardware solution security needs to be ensured throughout the whole solution life-cycle, from implementation until the decommissioning. This life-cycle can in some cases last for several decades. The rapid development of quantum computers has raised future threat for the eventual shattering of the security of the infrastructures that our daily digital lives, businesses, and democratic societies rely on. That is why hardware solutions designed and implemented today already need to, at the very minimum, have the capability to be upgraded to Post-Quantum Cryptography (PQC), or to already complement traditional asymmetric algorithms with PQC into a hybrid cryptographic system. Cryptographic modules should be designed to offer quantum-safe key exchange and digital signature operations, that ensure the security of our critical and personal information well into the foreseeable future. Read more about the quantum threat and Post-Quantum Cryptography.
Where are cryptographic modules used?
A hardware-based cryptographic module has multiple use cases, as it can be easily integrated to various systems for the purpose of offloading and accelerating cryptographic operations, and to act as a cryptographic coprocessor for System on Chips or to power secure communication between a microcontroller and other components.
Cryptographic modules can be used, for example, in a modern automotive system to authenticate and secure communications between various components, such as LIDAR and the Electronic Control Unit. They can also be implemented as the security core in an Authenticated or Secure Boot solution, to ensure the authenticity, integrity, and optionally confidentiality of the system boot image loaded during boot process. Adding secure key generation, storage, and management enables the implementation of a Hardware Root of Trust or a Hardware Security Module – the foundation of trust and security – in a hardware system.
Cryptographic modules are the beating heart of a hardware security system, and it is crucial to ensure they are implemented in the most secure and clean design possible. They offer a cost-effective and proven way to implement system security, enabling a design team to focus on the value-add functionality of the end product, without getting bogged down in the intricacies of cryptographic algorithms.
Learn more about cryptographic modules and Xiphera’s nQrux™ Crypto Module. The nQrux™ Crypto Module is tailored to meet specific customer security, performance, and area requirements for an optimal solution to implementing cryptographic operations in a hardware device.




