Xiphera releases extreme-speed IPsec (Internet Protocol security) IP (Intellectual Property) core. The new IP core completes the Security Protocols family providing protection for the layers 2, 3, and 4 of the OSI model. IPsec, on layer 3 (also known as the Network layer), secures the network traffic on the Internet Protocol layer, authenticating and encrypting Internet Protocol packets within a communication session.
IPsec protocol is widely used in various operating systems and network devices. It is most commonly used to secure communications in Virtual Private Networks (VPNs) over the Internet. Today’s hybrid and remote work environments are an excellent example of the importance of secure communications – IPsec secures network-to-network communications e.g. between sites, data centers, and businesses.
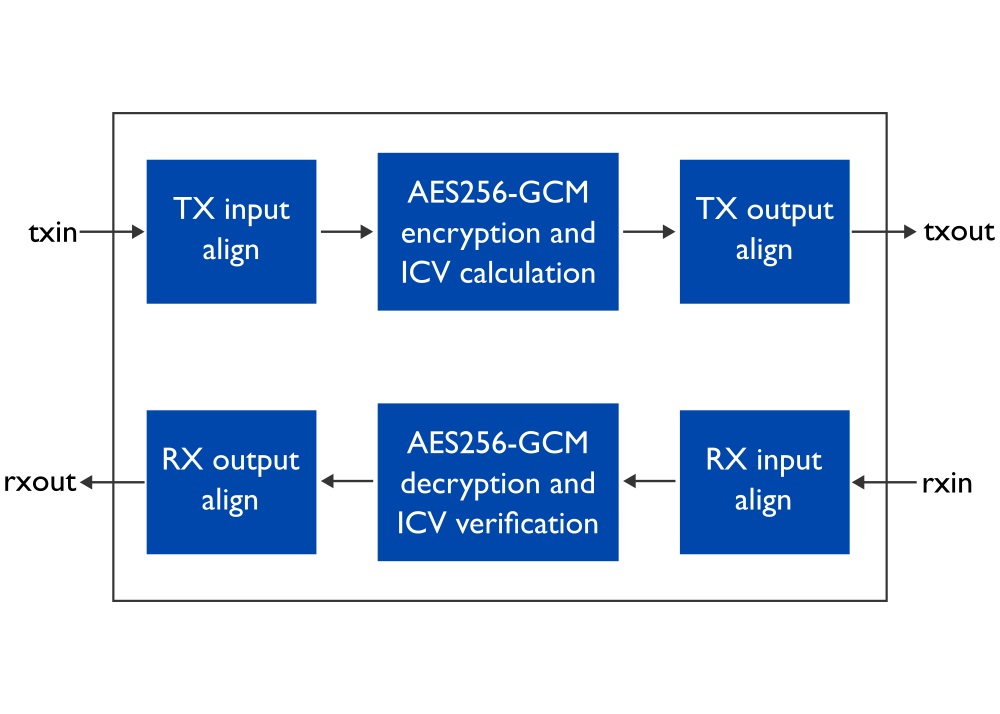
Xiphera’s extreme-speed IPsec IP core implements the ESP (Encapsulating Security Payload) frame processing of the IPsec protocol, using Xiphera’s own AES256-GCM IP core as its crypto engine to protect data confidentiality and integrity as well as data origin authentication. The IPsec core achieves a throughput exceeding 200 Gigabits per second (Gbps) in modern high-end FPGAs and ASICs, making it an excellent solution to secure traffic on links from 10 to 200 Gbps.
“Our IPsec offers scalable solution to meet the needed performance requirements by achieving full throughput with wanted linerate despite packet sizes. Latency of the IP is fixed, which is vital for timing critical applications”, says Tuomo Tarvainen, Xiphera’s System Architect.
For more information, visit the IPsec product page, or open the full product brief.
To learn more about how to secure your device communications with Xiphera’s Security Protocols – MACsec, IPsec, and TLS 1.3 – watch our webinar Cryptography at Work: Securing Device Communications.




