Xiphera expands support for SHA-3 (Secure Hash Algorithm) by launching two new Intellectual Property (IP) cores: the resource-optimised compact version XIP3030C and the performance-optimised version XIP3030H. XIP3030C requires less than one thousand Lookup Tables (LUTs) in a typical implementation. SHA-3 is significantly faster in hardware than SHA-2, and XIP3030H achieves a throughput of 40+ Gbps in high-end FPGAs.
Hashing is one of the fundamental operations in cryptography. It can be defined as a one-way function where an input message of an arbitrary size — for example, a file, a password, or the hash of a previous message — is mapped to a fixed-size output known as hash. Hash functions are widely used in various applications, for example in verifying the integrity of messages and files, generating and verifying digital signatures, verifying passwords, and also in blockchain technology. Additionally, hash functions are used in cryptographic primitives such as Pseudorandom Number Generators (PRNGs) and Message Authentication Codes (MACs).
“One of the main features of Xiphera’s new SHA-3 IP cores is their versatile algorithm support,” says Kimmo Järvinen, Co-founder and CTO of Xiphera. “Both IP cores support all four variants of SHA-3 hashing algorithms (224, 256, 384, and 512 bits) as well as SHAKE and cSHAKE, and even its derivatives KMAC, TupleHash, and ParallelHash.”
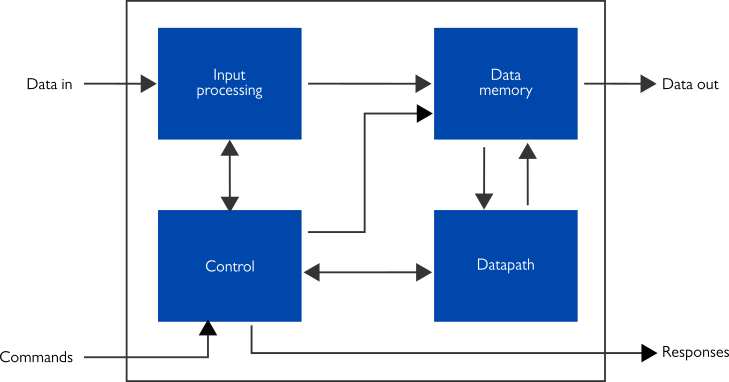
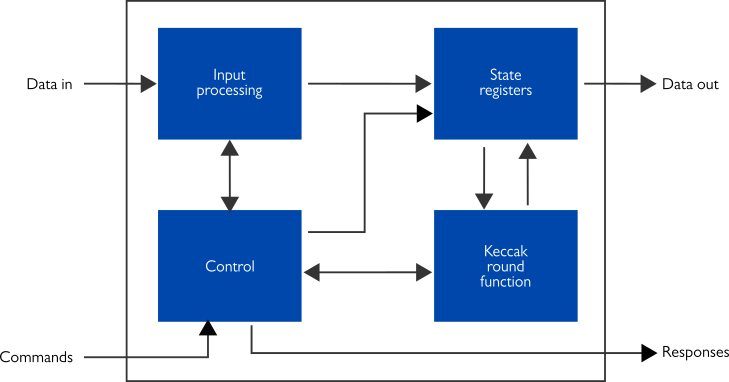
Additionally, XIP3030C and XIP3030H have an identical pin-out allowing for designs where either one of the IP cores can be instantiated without affecting the rest of the design, including software drivers.
“The identical pin-out of the two new SHA-3 IP cores opens up interesting possibilities for system designers”, Kimmo Järvinen describes. “It allows for trade-offs where a compact solution with XIP3030C can be easily changed to XIP3030H that offers very high hashing speeds if a need emerges.”
“SHA-3 is used in numerous applications in today’s cryptographic systems, and an important use case is the soon-to-be-launched set of PQC (Post-Quantum Cryptography) algorithms, which internally use many different variants of SHA-3”, Järvinen concludes.
For more information, visit the product pages for the SHA-3 compact version XIP3030C and the high-speed version XIP3030H. Don’t forget to download the full product briefs for XIP3030C and XIP3030H.
Read more about cryptographic hash functions and see all Xiphera’s solutions in this category at our Cryptographic Hash Functions page. Don’t hesitate to contact us at sales(at)xiphera.com.