nQrux® CCE
Confidential Computing Engine
Tailored confidential computing infrastructures for...
AI processing and remote code execution
Satellite and mission-critical applications
Remote use of accelerator IP cores in FPGA farms
Industrial and IoT environments
Key features
Complete physical isolation of code & data
Secure code & data transmission with TLS 1.3
Quantum-secure crypto option
Versatile computational enclave:
RISC-V or customer-specific cores
Application-specific accelerators
- Tailored based on application, security, and performance requirements
For FPGA and ASIC implementations
Technical specifications
nQrux® Confidential Computing Engine
Product code: XIP7700 Secure code and data transmission
TLS 1.3 protocol with:
CPU
RISC-V
Optional customer-specific core
Accelerators
Specified and implemented according to requirements
Post-Quantum Cryptography
For more technical details, including FPGA resources & peak performance as well as ordering instructions, send us a message.
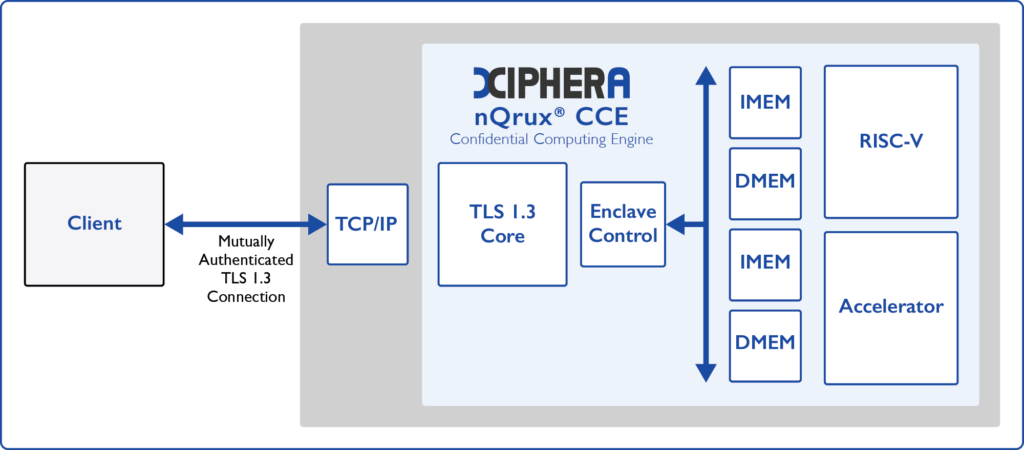
CCE and TLS 1.3
Communication of data and code to the CCE is protected with hardware-based TLS 1.3. Access policies are enforced with hardware isolation of resources and TLS 1.3 client-authentication, so that only clients with appropriate certificates are allowed to access specific resources.

