ECDH/ECDSA: NIST Curves
Xiphera’s compact IP cores implement ECDH and ECDSA on NIST prime curves, and the high-speed ECC Accelerator reaches over thousand operations per second.
Xiphera’s NIST Curves and ECC Accelerator for ECDH/ECDSA provide cutting-edge security solutions designed for robust public-key operations, including encryption, digital signatures, and key exchanges. These solutions are optimised for both performance and resource efficiency in both FPGA and ASIC implementations, offering versatile functionality across various cryptographic protocols.
Versatile solutions for secure environments in…
Secure data communications
Digital signature verification
Key exchange protocols
High-performance cryptographic operations
Key features
- Optimised resource requirements
- High throughput
- Compliant with FIPS 186-5 and SP 800-56A
- Supports NIST P curves
- Secure architecture with side-channel protections
- Fully RTL-based with no CPU or software components
- Efficient and optimised architecture
- Easy system integration
- Vendor agnostic FPGA/ASIC implementation
Technical specifications
The IP cores implement ECDH and ECDSA, and the ECC Accelerator demonstrates a capability of executing over a thousand operations per second when deployed on a modern FPGA or ASIC.
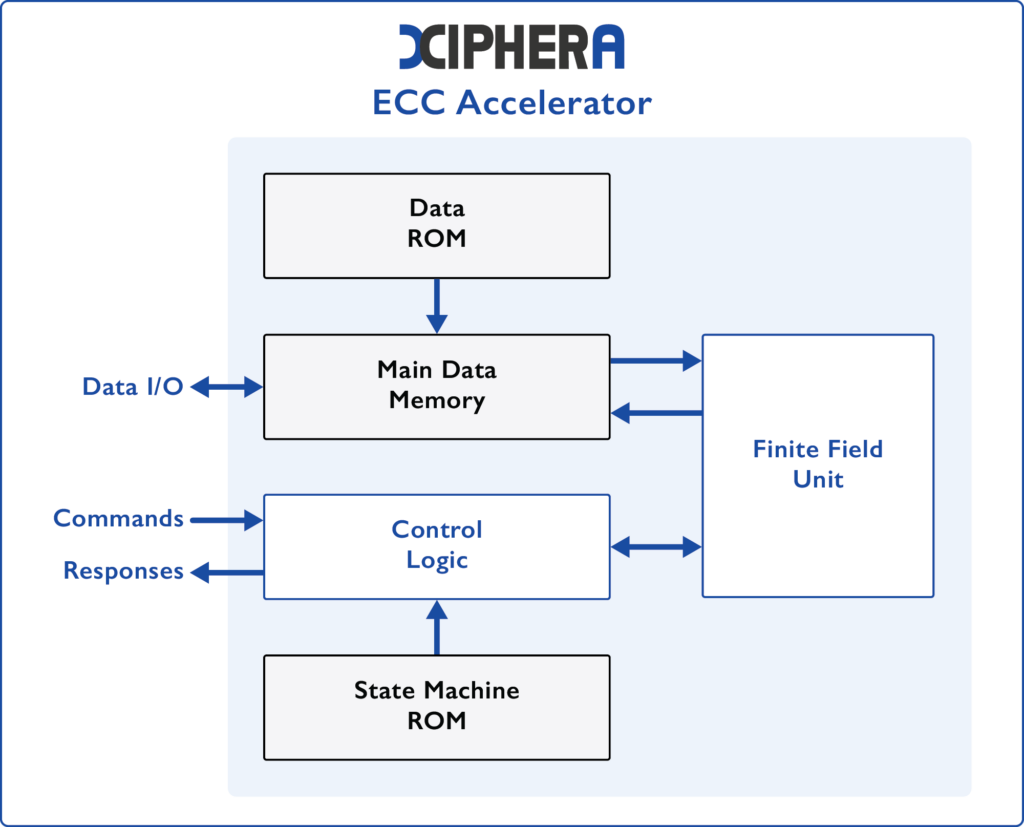
High-speed ECC Accelerator
Product code: XIP4200H
- >1K ops/sec for key generation on NIST P-256
- ~36 kLUTs
- Supports all NIST P Curves
- Protections against multi-trace side-channel attacks
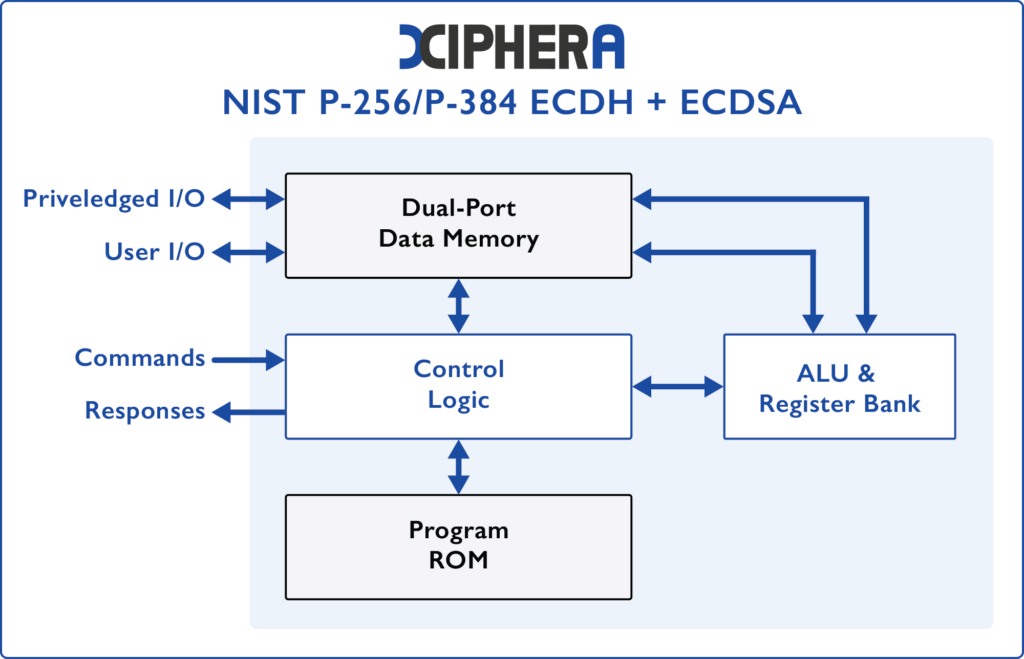
Compact NIST P-224/256/384/521 ECDH & ECDSA
Product code: XIP41X3C
- Several 100s key agreements or signatures/sec
- ~1.12 kLUTs
Product brief
Learn more about the key features and functionalities of the NIST Curves and ECC Accelerator for ECDH/ECDSA.
Resource sheet
Download the resource sheet to learn more about the FPGA and ASIC resource requirements and performance.
Quantum-resilient secure boot

